BOUNDLESS IMMIGRATION Exceeded All Our Expectations
We are so happy and amazed with how much service we’ve received from Boundless, especially Nerissa. It has been a Godsent that we found Boundless. We prayed for help and God answered our…
Rhea Da
My heartfelt gratitude to Boundless and…
My heartfelt gratitude to Boundless and its team; I have no words to express my appreciation. Please let me know if there is anything more than a five-star recommendation, and I will give it…
Scofield JG Isibor
Boundless Always Answers
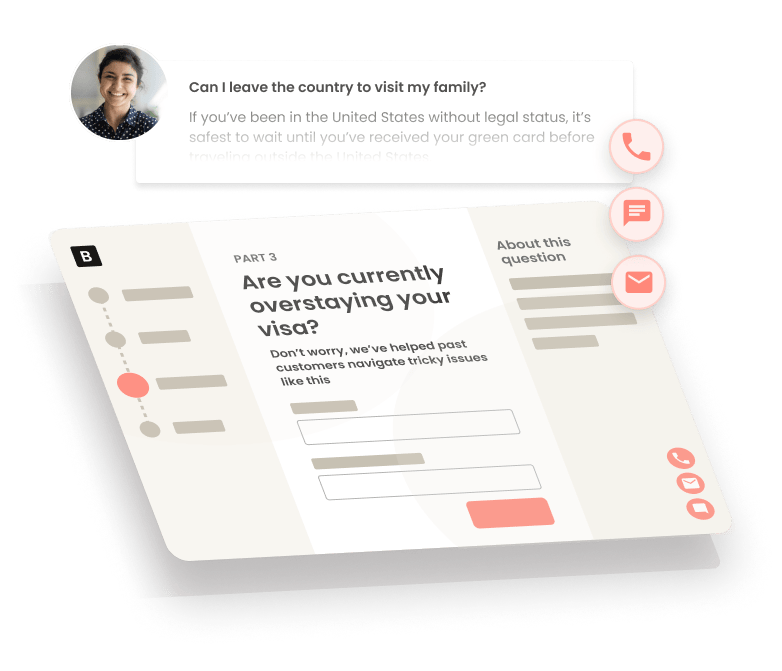
Even after the whole process with Boundless finished, they always answer my questions. We are nearing the interview process and Boundless answers all our questions and eases our stress. One…
Jenna
Well organized, professional and cheaper then a lawyer
Where all immigration lawyer where super expensive, Boundless was more in my budget, and they have made the process so easy, they follow you step by step and always answer if i had a question…
Antoine Blandin
Heartfelt Thanks to the Exceptional Boundless Team
The Boundless team displayed exceptional professionalism throughout my green card application process. They excelled in tasks such as document review, promptly addressing my queries, providing…
Mohamed Elmahdy
I have been with boundless since 2022…
I have been with boundless since 2022 of September. They did all i130 for my spouse and did a great job as it got approved with no RFE’s and was approved within 10.5 months. They are…
Dastagir Hussain
It was a very good experience
It was a very good experience. I felt prepared for my interview and I did not have to worry about all the paperwork.
Theresa Brown
They will definitely help you achieve your green card dream.
Thank you so much ELLISON for taking time to answer all my question. You knew your niche and im grateful you are the one who answered my call. Great job. You are so patient , knowledgable and…
Delia Evered
Great service!!
Great service, super detailed filing, and exceptional legal assistance throughout. They also have a WhatsApp messaging chat system where you can ask questions to their customer service teams…
zaddy bangtan
Boundless Delivered on their Promises
What I expected from Boundless was exactly what I got. The team provided me with a streamlined “turbo-tax” type experience where I answered simple questions, then they used those answers to…
Joshua Kilpatrick
Extremely thankful for the Boundless team
Made my immigration journey stress free, time saving and the team was available to answer my questions. In less than a minute, I had an agent answering my question. They make sure the final…
Coralie
Outstanding Customer Service
Due to personal circumstances my application was inadvertently delayed. I am delighted to say that Boundless acted in a generous and professional manner in resolving the situation and I have…